Insider Threat Plan Template
Insider Threat Plan Template - Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the department's mission,. However, most maligned insiders exhibit risky. On cisa.gov, visitors will find. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web an incident response plan or ir plan is a set of tools and processes startups can leverage to detect, eliminate and recover from cyber threats. More industry insider threat information and resources. Guy bunker from clearswift states that:. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web june 9, 2021 the diplomatic security service manages/administers the department of state’s insider threat program to protect the department, its people,. Insider threat indicators in uam june 2023, 7. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web how can you identify an insider threat? On cisa.gov, visitors will find. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. The goal of the ir plan is to help. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web partners can use cteps to initiate discussions within their organizations about their ability to address a variety of threat scenarios. The goal of the ir plan is to help the. Web how can you identify an. Web ey’s insider threat program framework helps organizations develop an integrated risk management program to protect their critical assets against insider threats. Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the department's mission,. Defining the threat, detecting and identifying the threat,. Specifically, the program must gather, integrate, and report relevant and. Web an incident response plan or ir plan is a set of tools and processes startups can leverage to detect, eliminate and recover from cyber threats. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. More industry insider threat information and resources. Web ey’s. Web ey’s insider threat program framework helps organizations develop an integrated risk management program to protect their critical assets against insider threats. Every single business owner risks the. Web partners can use cteps to initiate discussions within their organizations about their ability to address a variety of threat scenarios. Web the insider threat mitigation guide provides comprehensive information to help. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Web cisa defines insider threat as the threat that an insider will use their authorized access, wittingly or unwittingly, to do harm to the department’s mission, resources, personnel,. Web september is national insider threat awareness month, but business owners must always keep insider threat in. Web how can you identify an insider threat? Web communications plan & messaging packet dod insider threat program, office of the under secretary of defense for intelligence and security ousd (i&s) 1. Web june 9, 2021 the diplomatic security service manages/administers the department of state’s insider threat program to protect the department, its people,. However, most maligned insiders exhibit risky.. Web september is national insider threat awareness month, but business owners must always keep insider threat in mind. Web the first step in creating this plan is to accept the reality and recognize that an incident response plan is a business imperative. Web cisa defines insider threat as the threat that an insider will use their authorized access, wittingly or. Web june 9, 2021 the diplomatic security service manages/administers the department of state’s insider threat program to protect the department, its people,. However, most maligned insiders exhibit risky. Web an insider threat program is “a coordinated group of capabilities under centralized management that is organized to detect and prevent the unauthorized. Web partners can use cteps to initiate discussions within. Web partners can use cteps to initiate discussions within their organizations about their ability to address a variety of threat scenarios. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to. On cisa.gov, visitors will find. Specifically, the program must gather, integrate, and report relevant and. More industry insider threat information and resources. Web ey’s insider threat program framework helps organizations develop an integrated risk management program to protect their critical assets against insider threats. Web september is national insider threat awareness month, but business owners must always keep insider threat in mind. However, most maligned insiders exhibit risky. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Web june 9, 2021 the diplomatic security service manages/administers the department of state’s insider threat program to protect the department, its people,. Every single business owner risks the. Web communications plan & messaging packet dod insider threat program, office of the under secretary of defense for intelligence and security ousd (i&s) 1. Web 1to establish and maintain an insider threat program to detect, deter and mitigate insider threats. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web how can you identify an insider threat? Web the first step in creating this plan is to accept the reality and recognize that an incident response plan is a business imperative. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the department's mission,. Web dcsa continues to assess compliance with minimum insider threat requirements, which provide the basic elements necessary to establish a fully functional insider threat. Web an incident response plan or ir plan is a set of tools and processes startups can leverage to detect, eliminate and recover from cyber threats. Web partners can use cteps to initiate discussions within their organizations about their ability to address a variety of threat scenarios. Web an insider threat program is “a coordinated group of capabilities under centralized management that is organized to detect and prevent the unauthorized. Web an incident response plan or ir plan is a set of tools and processes startups can leverage to detect, eliminate and recover from cyber threats. On cisa.gov, visitors will find. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Guy bunker from clearswift states that:. The goal of the ir plan is to help the. Specifically, the program must gather, integrate, and report relevant and. Web september is national insider threat awareness month, but business owners must always keep insider threat in mind. Web an “insider threat” is now defined as the threat that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the department's mission,. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. There is no foolproof formula for identifying or predicting an insider threat; Web communications plan & messaging packet dod insider threat program, office of the under secretary of defense for intelligence and security ousd (i&s) 1. Web how can you identify an insider threat? Web partners can use cteps to initiate discussions within their organizations about their ability to address a variety of threat scenarios. Web dcsa continues to assess compliance with minimum insider threat requirements, which provide the basic elements necessary to establish a fully functional insider threat. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments;Building an Insider Threat Management Program Divurgent
Insider Threat Report SC Report Template Tenable®
building an insider threat program Risk Management Monitor
Insider Threat Program Template Template Resume Examples QBD3E4RYOX
Example Insider Threat Program Organizational Structure and Data
Insider Threat Program What It Is & Checklist for Building One Ekran
Insider Threat Plan Template Master of Documents
Insider Threat Program Template Template Resume Examples QBD3E4RYOX
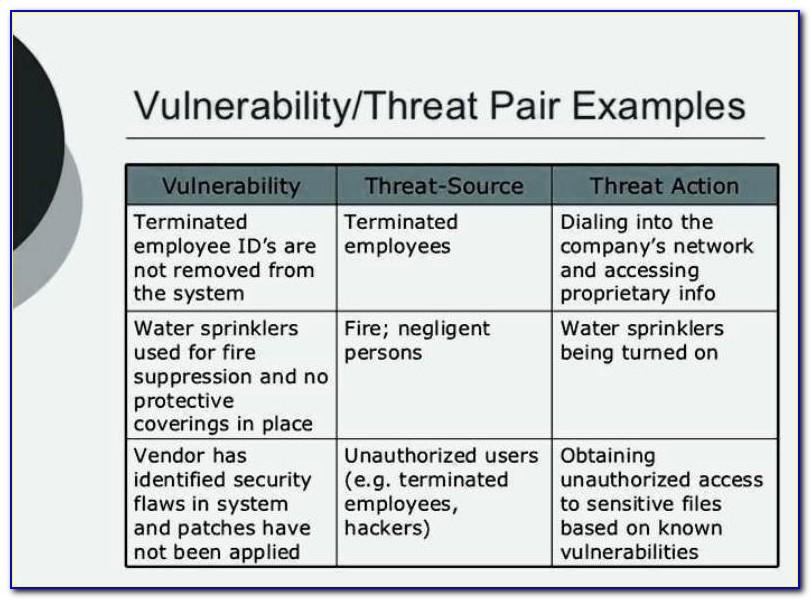
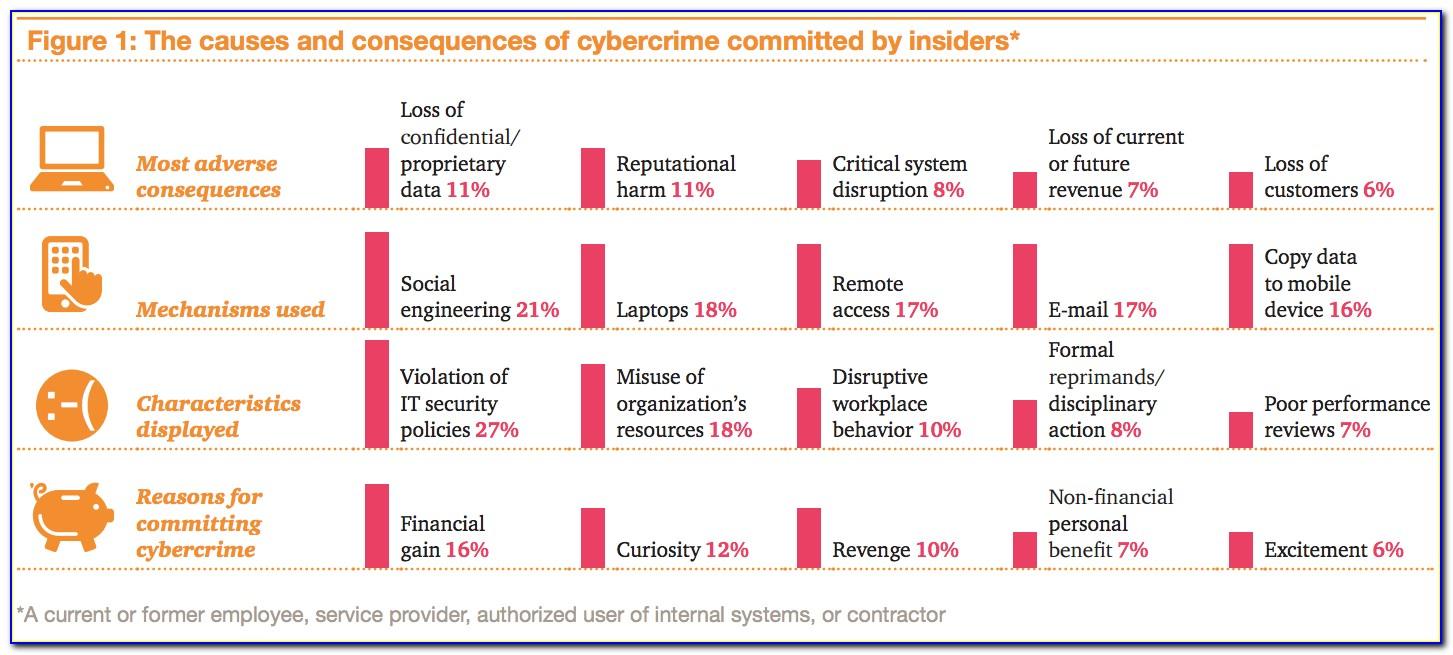
How to Prevent Insider Threats Case Studies, Examples, Types
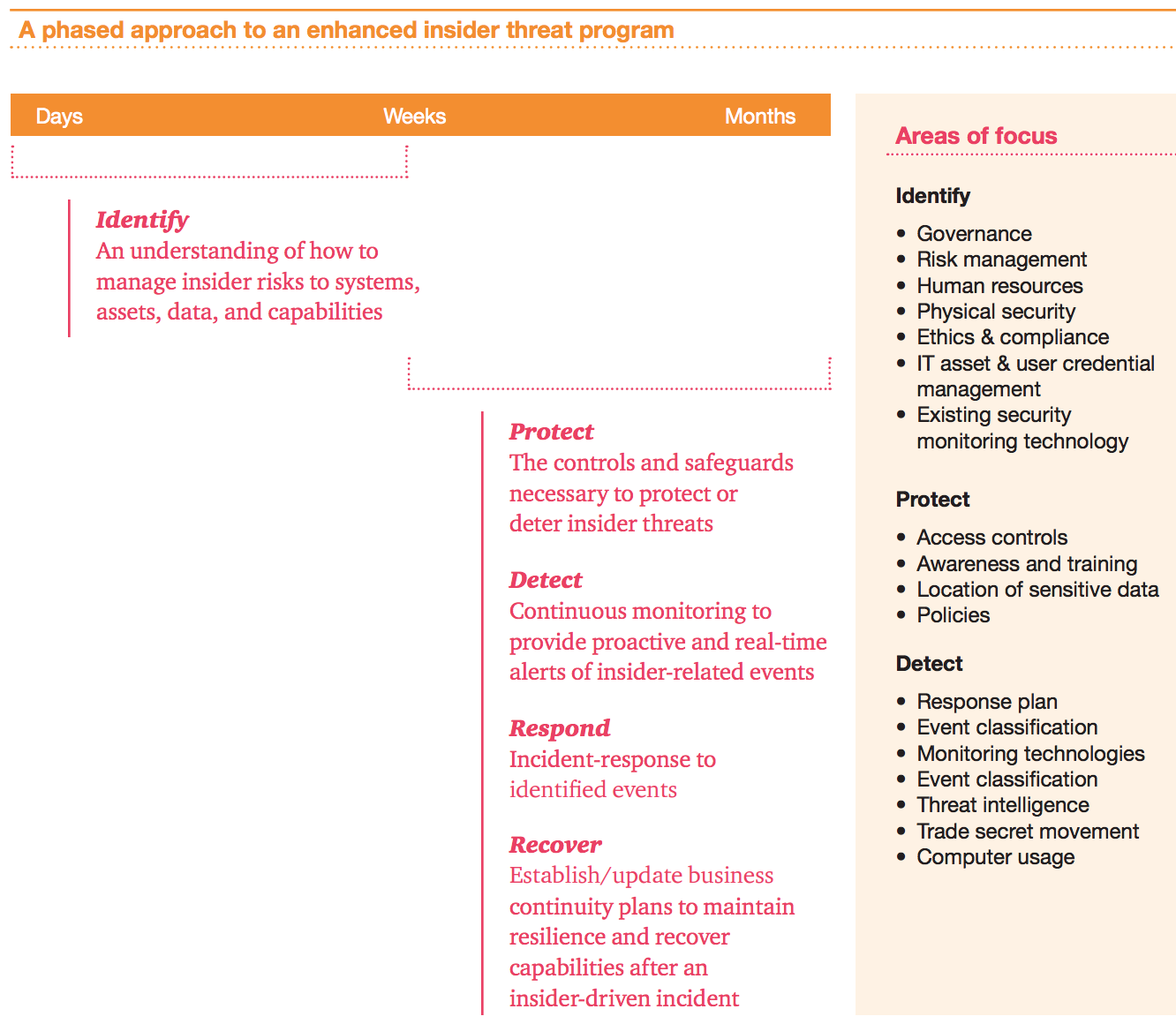
Insider Threat Mitigation
Web June 9, 2021 The Diplomatic Security Service Manages/Administers The Department Of State’s Insider Threat Program To Protect The Department, Its People,.
However, Most Maligned Insiders Exhibit Risky.
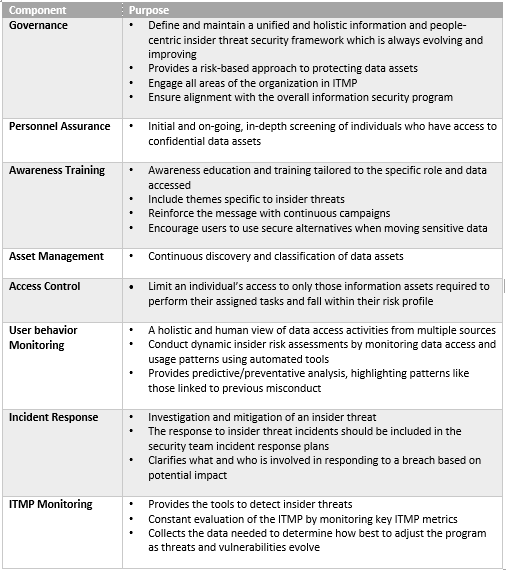
Web Ey’s Insider Threat Program Framework Helps Organizations Develop An Integrated Risk Management Program To Protect Their Critical Assets Against Insider Threats.
Web 1To Establish And Maintain An Insider Threat Program To Detect, Deter And Mitigate Insider Threats.
Related Post: