Pam Policy Template
Pam Policy Template - Web one of the first steps to privileged access management (pam) success is defining clear and consistent policies that everyone who uses and manages privileged accounts. Web a pam solution identifies the people, processes, and technology that require privileged access and specifies the policies that apply to them. It is common for the. Web pam policy is a subset of cybersecurity policies that deal with privileged access. Web updated august 13, 2023. There are all kinds of. Web deloitte’s privileged access management (pam) service helps you stay in control of your most valuable assets. Web privileged access management (pam) helps organizations manage their privileged accounts in order to protect their critical assets, meet compliance regulations and to. Your pam solution must have. Web 6 steps for complete pam & beyond. Web 6 steps for complete pam & beyond. Web the exact templates you need to effectively manage your project will be unique to you and the type, size, and complexity of your project. A property management agreement is between a property owner and a manager that is hired to maintain the property. Please refer to these resources when preparing documents. Web updated august 13, 2023. Web publishing guidelines the army publishing directorate (apd) uses the following references and style manuals. It is common for the. There are all kinds of. Web a project management agreement is a specific type of service agreement, whereby a client hires someone to oversee and manage a project for them (that person. Web this article walks you through the process of deciding which roles to manage through pam, and how to define them with appropriate permissions and restrictions. Our pam team becomes an extension of your existing security. Web deloitte’s privileged access management (pam) service helps you stay in control of your most valuable assets. Web pam policy is a subset of. They are based on compliance requirements outlined by cis, nist, pci and. Web 6 steps for complete pam & beyond. Please refer to these resources when preparing documents for. Web a pam solution identifies the people, processes, and technology that require privileged access and specifies the policies that apply to them. There are all kinds of. Web a project management agreement is a specific type of service agreement, whereby a client hires someone to oversee and manage a project for them (that person. Web you can use this sample policy as a starting point to build a pam policy for your organization. Web this article walks you through the process of deciding which roles to manage. They are based on compliance requirements outlined by cis, nist, pci and. Web 6 steps for complete pam & beyond. Pam policies determine which users can have privileged access to specific systems, when,. Web pam policy is a subset of cybersecurity policies that deal with privileged access. Web updated august 13, 2023. Web a property management agreement is a document used by a property owner to hire a company or person to manage the rental of their property. They are based on compliance requirements outlined by cis, nist, pci and. Pam policies determine which users can have privileged access to specific systems, when,. Web deloitte’s privileged access management (pam) service helps you. Web a property management agreement is a document used by a property owner to hire a company or person to manage the rental of their property. Web deloitte’s privileged access management (pam) service helps you stay in control of your most valuable assets. Web this article walks you through the process of deciding which roles to manage through pam, and. Please refer to these resources when preparing documents for. Pam policies determine which users can have privileged access to specific systems, when,. Web a project management agreement is a specific type of service agreement, whereby a client hires someone to oversee and manage a project for them (that person. Web getting this easily customizable sample policy as a starting point. Web a pam solution identifies the people, processes, and technology that require privileged access and specifies the policies that apply to them. There are all kinds of. It is common for the. Da form 1222, da form 200, da form 209, da form. Web updated august 13, 2023. Web deloitte’s privileged access management (pam) service helps you stay in control of your most valuable assets. Web a project management agreement is a specific type of service agreement, whereby a client hires someone to oversee and manage a project for them (that person. Web 6 steps for complete pam & beyond. Pam policies determine which users can have privileged access to specific systems, when,. Da form 1222, da form 200, da form 209, da form. Web pam policy is a subset of cybersecurity policies that deal with privileged access. Our pam team becomes an extension of your existing security. Web getting this easily customizable sample policy as a starting point to create a privileged access betriebswirtschaft (pam) policy for your arrangement. Web privileged access management (pam) helps organizations manage their privileged accounts in order to protect their critical assets, meet compliance regulations and to. A property management agreement is between a property owner and a manager that is hired to maintain the property. Web this article walks you through the process of deciding which roles to manage through pam, and how to define them with appropriate permissions and restrictions. It is common for the. Web a property management agreement is a document used by a property owner to hire a company or person to manage the rental of their property. Web a pam solution identifies the people, processes, and technology that require privileged access and specifies the policies that apply to them. Web one of the first steps to privileged access management (pam) success is defining clear and consistent policies that everyone who uses and manages privileged accounts. Please refer to these resources when preparing documents for. Your pam solution must have. Web the exact templates you need to effectively manage your project will be unique to you and the type, size, and complexity of your project. Web you can use this sample policy as a starting point to build a pam policy for your organization. There are all kinds of. Web privileged access management (pam) helps organizations manage their privileged accounts in order to protect their critical assets, meet compliance regulations and to. Web deloitte’s privileged access management (pam) service helps you stay in control of your most valuable assets. Pam policies determine which users can have privileged access to specific systems, when,. Your pam solution must have. Web a project management agreement is a specific type of service agreement, whereby a client hires someone to oversee and manage a project for them (that person. Web updated august 13, 2023. It is common for the. Web the exact templates you need to effectively manage your project will be unique to you and the type, size, and complexity of your project. Da form 1222, da form 200, da form 209, da form. Web 6 steps for complete pam & beyond. Our pam team becomes an extension of your existing security. Web a pam solution identifies the people, processes, and technology that require privileged access and specifies the policies that apply to them. Web this article walks you through the process of deciding which roles to manage through pam, and how to define them with appropriate permissions and restrictions. Web you can use this sample policy as a starting point to build a pam policy for your organization. Web a property management agreement is a document used by a property owner to hire a company or person to manage the rental of their property. They are based on compliance requirements outlined by cis, nist, pci and.FREE Blank Business Plan Template Download in Word, Google Docs
what is pam contract
Privileged Access Management or PAM
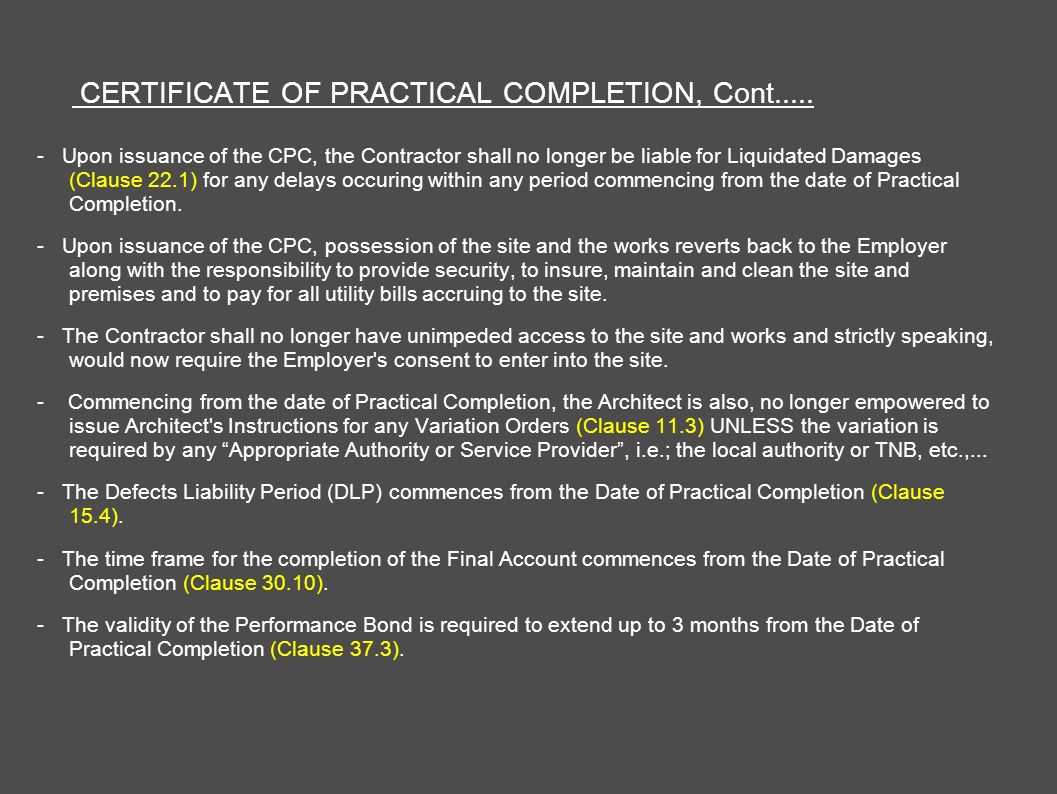
Pam Standard Form Of Contract / Completion of works in accordance with
PAM Contracts AGREEMENT AND CONDITIONS OF PAM SUBCONTRACT 2006
Free Company Policy Template Of 10 Sample Pany Policy Templates
Privileged Access Management Why and How to Prioritize It
Architect's Certification Under The Pam Contract 2006 within Practical
Form 30C Fill Out and Sign Printable PDF Template signNow
(PDF) The assessment of comparative advantage of the nonruminant
There Are All Kinds Of.
Web One Of The First Steps To Privileged Access Management (Pam) Success Is Defining Clear And Consistent Policies That Everyone Who Uses And Manages Privileged Accounts.
Web Pam Policy Is A Subset Of Cybersecurity Policies That Deal With Privileged Access.
Web Publishing Guidelines The Army Publishing Directorate (Apd) Uses The Following References And Style Manuals.
Related Post: