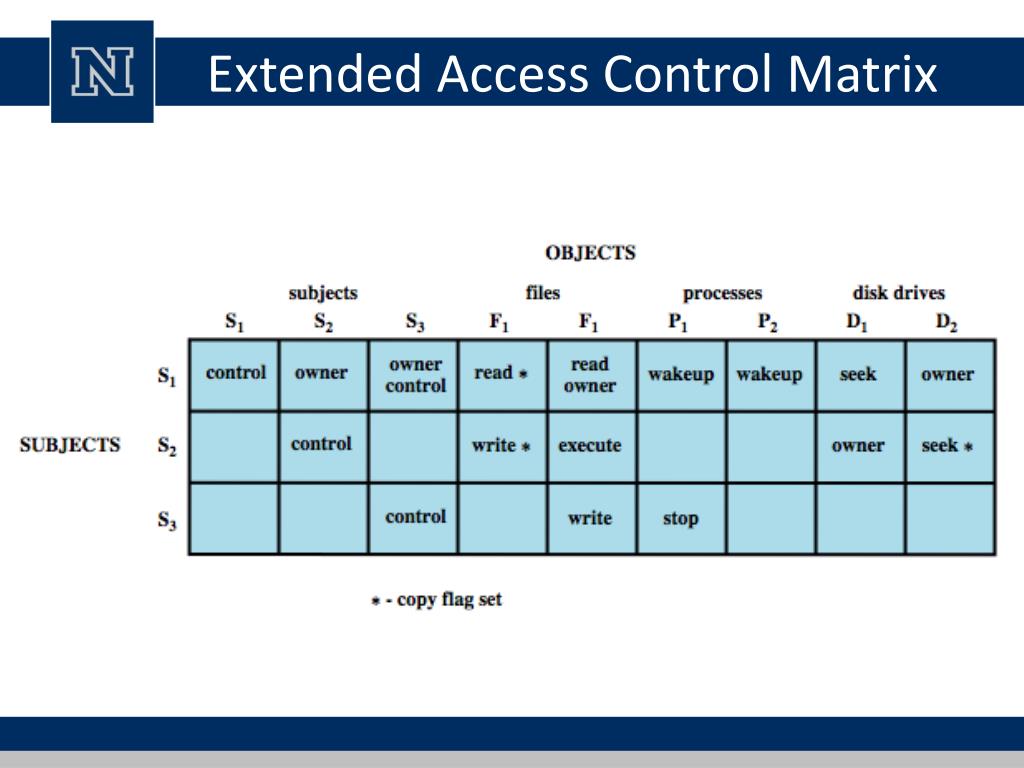
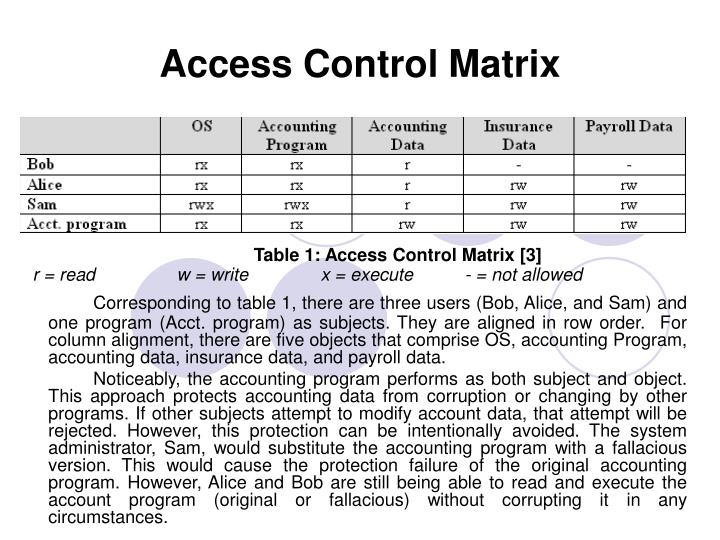
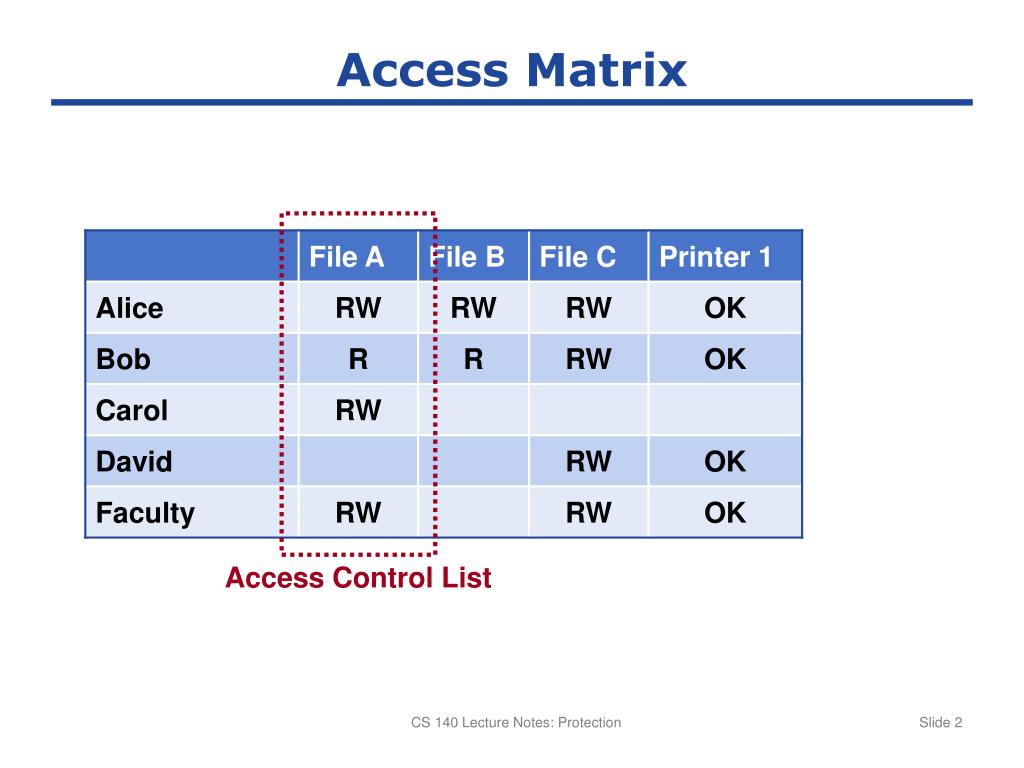
Role Based Access Control Matrix Template
Role Based Access Control Matrix Template - Web view access control as a matrix. Web role based access control. For information about roles and scope, see roles, scope, and context. Web the rbac model there are three types of access control under the rbac standard: They help the practitioner ensure that the access control. Core rbac the core model outlines the. This is the first step in role creation. Using azure rbac, you can segregate duties. The rbac role engineering process describes the. It creates a very tight permission system with firm. Web view access control as a matrix. All other roles' scope is limited to their organization. Two ways to slice the. It creates a very tight permission system with firm. Web role based access control. Web this rbac role engineering process document describes the methodology that the task force will follow in pursuing its goal. Use this template to outline the roles for your organization. Using azure rbac, you can segregate duties. Web role based access control. Web as a security architecture concept, rbac matrices are a way of representing access control strategies visually. Web this rbac role engineering process document describes the methodology that the task force will follow in pursuing its goal. •a user has a permission only if the user has an authorized role which is associated with that permission. All other roles' scope is limited to their organization. Web the rbac model there are three types of access control under. For information about roles and scope, see roles, scope, and context. The rbac role engineering process describes the. Cyb 200 module four activity template after reviewing the. You can easily edit this template using creately. All other roles' scope is limited to their organization. Two ways to slice the. In this quickstart, you create a resource group and grant a. Core rbac the core model outlines the. All other roles' scope is limited to their organization. Cyb 200 module four activity template after reviewing the. They help the practitioner ensure that the access control. Web as a security architecture concept, rbac matrices are a way of representing access control strategies visually. This is the first step in role creation. For information about roles and scope, see roles, scope, and context. You can export it in multiple formats like jpeg, png and svg and easily add. Use this template to define if each role. •a user has a permission only if the user has an authorized role which is associated with that permission. You can easily edit this template using creately. For information about roles and scope, see roles, scope, and context. The rbac role engineering process describes the. Use this template to outline the roles for your organization. In this quickstart, you create a resource group and grant a. Core rbac the core model outlines the. Cyb 200 module four activity template after reviewing the. Web this rbac role engineering process document describes the methodology that the task force will follow in pursuing its goal. •a user has a permission only if the user has an authorized role which is associated with that permission. It creates a very tight permission system with firm. Use this template to outline the roles for your organization. Use this template to define if each role. Core rbac the core model outlines the. Web the rbac model there are three types of access control under the rbac standard: •a user has a permission only if the user has an authorized role which is associated with that permission. They help the practitioner ensure that the access control. Core rbac the core model outlines the. Use this template to outline the roles for your organization. You can export it in multiple formats like jpeg, png and svg and easily add it to word. Use this template to define if each role. Two ways to slice the. Web •roles are associated with permissions. Web role based access control. It is used by the majority of medium to. It creates a very tight permission system with firm. The rbac role engineering process describes the. Using azure rbac, you can segregate duties. This is the first step in role creation. Cyb 200 module four activity template after reviewing the. For information about roles and scope, see roles, scope, and context. In this quickstart, you create a resource group and grant a. Web as a security architecture concept, rbac matrices are a way of representing access control strategies visually. You can easily edit this template using creately. •a user has a permission only if the user has an authorized role which is associated with that permission. All other roles' scope is limited to their organization. Web this rbac role engineering process document describes the methodology that the task force will follow in pursuing its goal. Use this template to outline the roles for your organization. After reviewing the scenario in. Cyb 200 module four activity template after reviewing the. It creates a very tight permission system with firm. In this quickstart, you create a resource group and grant a. This is the first step in role creation. After reviewing the scenario in. Using azure rbac, you can segregate duties. Web the rbac model there are three types of access control under the rbac standard: It is used by the majority of medium to. They help the practitioner ensure that the access control. All other roles' scope is limited to their organization. Web this rbac role engineering process document describes the methodology that the task force will follow in pursuing its goal. Use this template to define if each role. You can export it in multiple formats like jpeg, png and svg and easily add it to word. The rbac role engineering process describes the. Web •roles are associated with permissions. Web as a security architecture concept, rbac matrices are a way of representing access control strategies visually.PPT Chapter 9 Database Security PowerPoint Presentation, free
PPT IS 2150 / TEL 2810 Information Security and Privacy PowerPoint
PPT Computer Security Principles and Practice PowerPoint
5 Document Control Template Excel Excel Templates
Access Control Matrix Excel Template Login Information, AccountLoginask
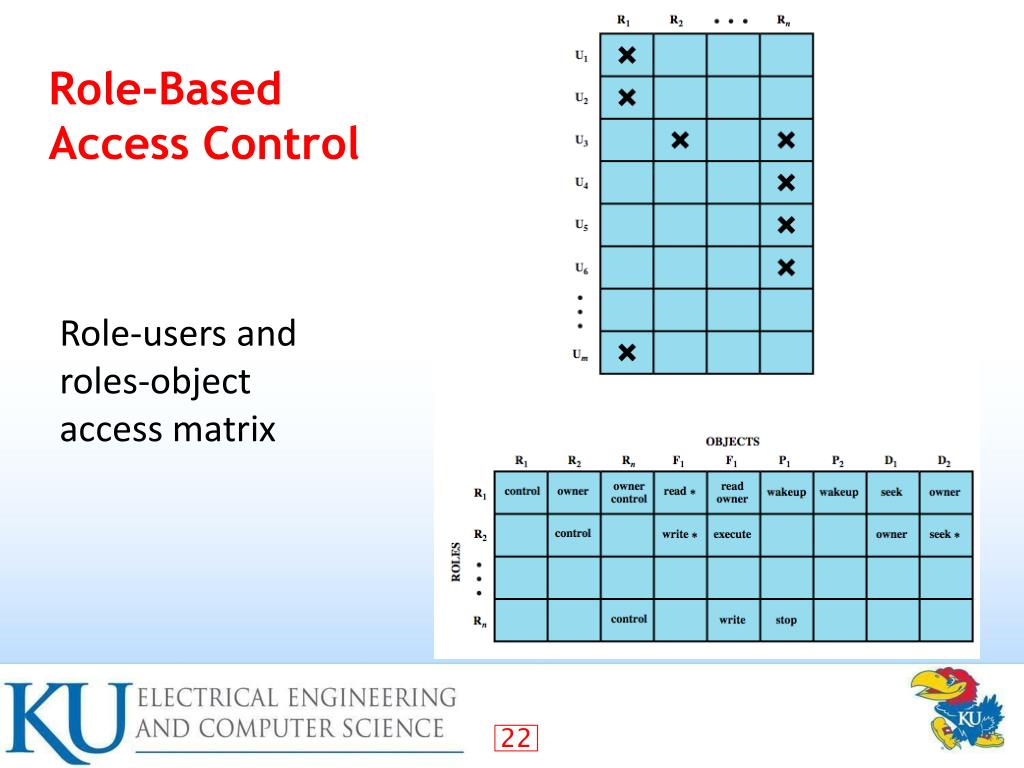
RoleBased Access Control (RBAC) CyberHoot
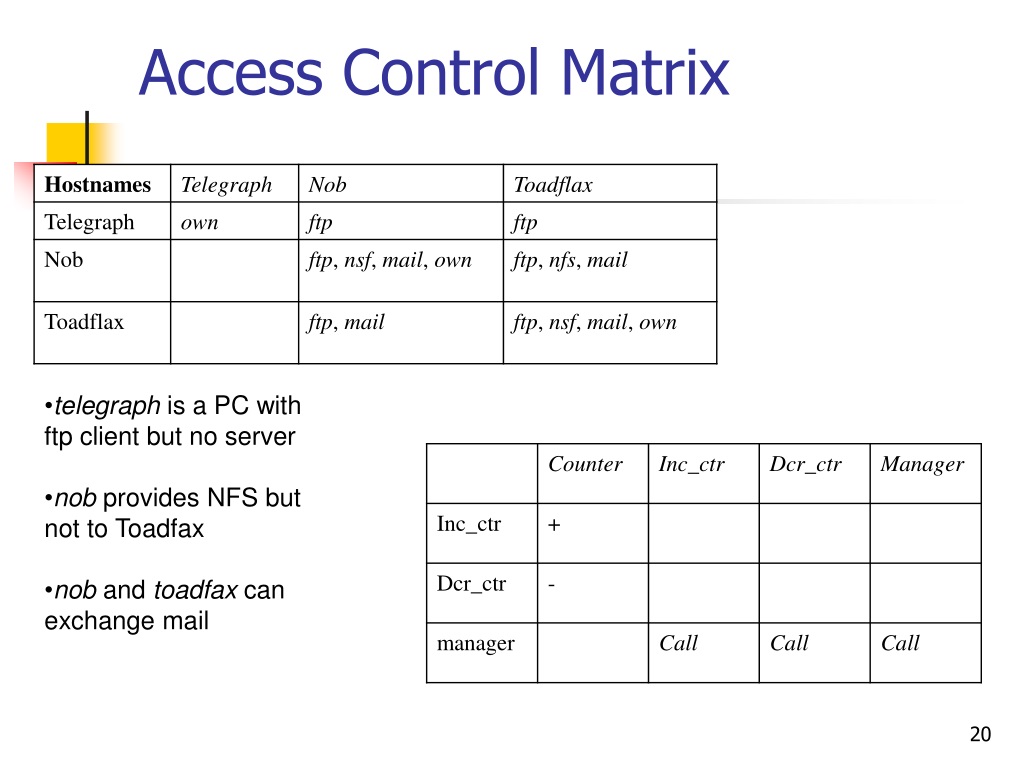
PPT Lecture 7 Access Control PowerPoint Presentation, free download
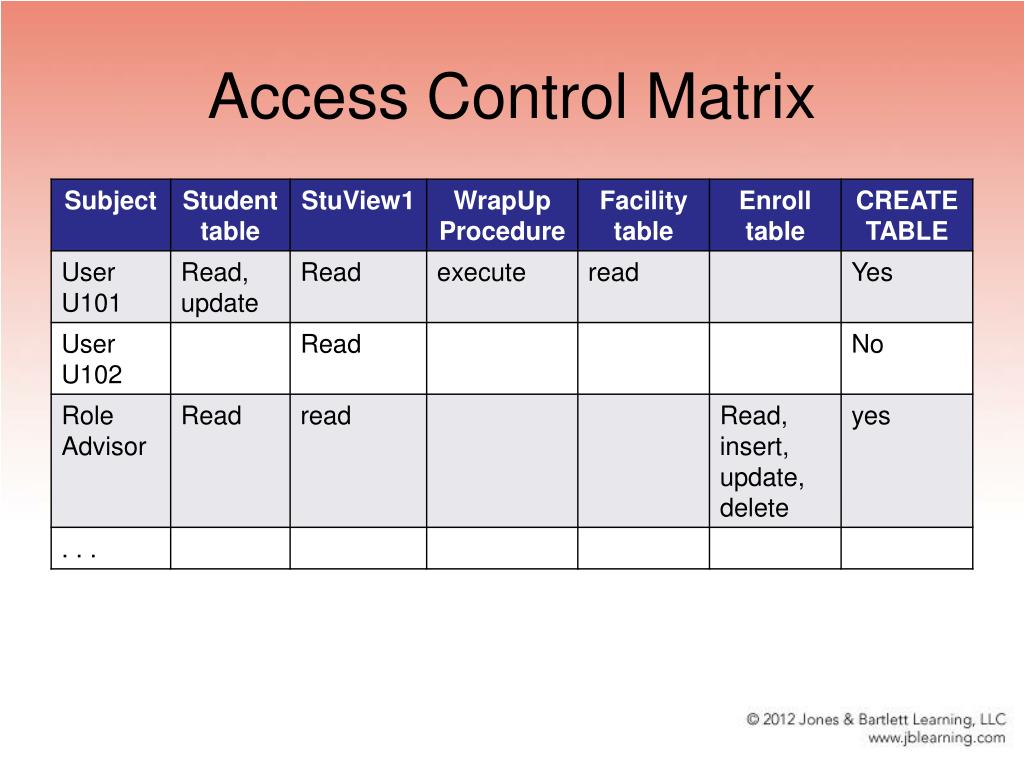
PPT Access Control Matrix PowerPoint Presentation ID5507190
RoleBased Access Control (RBAC). RoleBased Access Control (RBAC) by
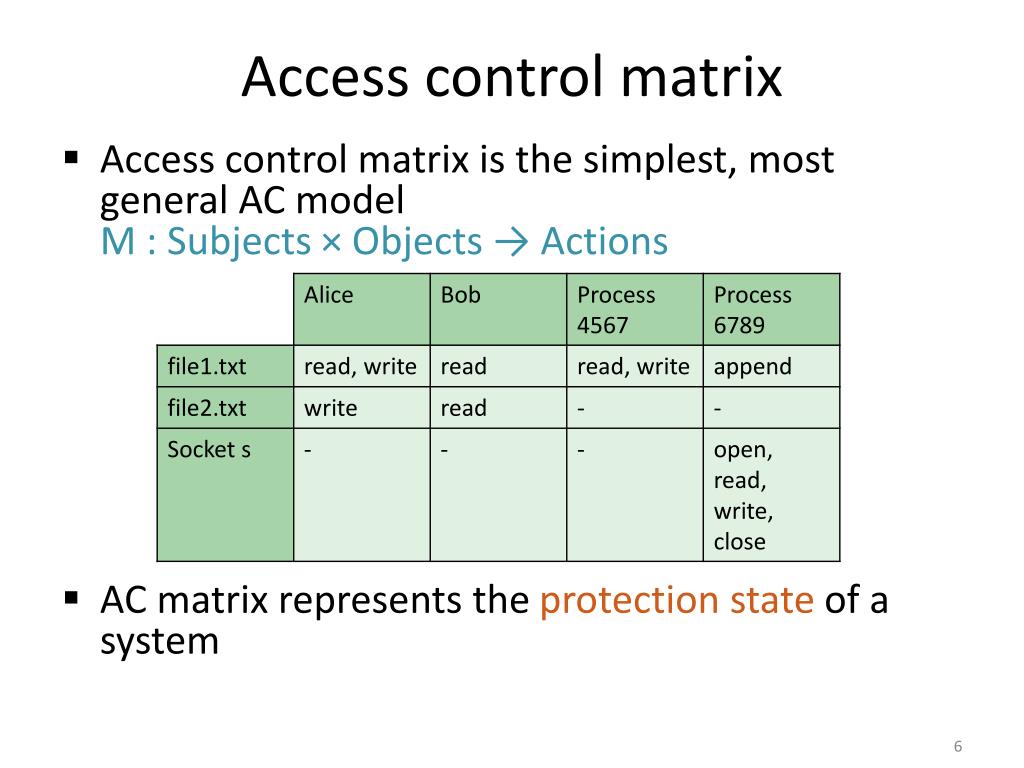
PPT Access Matrix PowerPoint Presentation, free download ID4662709
•A User Has A Permission Only If The User Has An Authorized Role Which Is Associated With That Permission.
Two Ways To Slice The.
Use This Template To Outline The Roles For Your Organization.
You Can Easily Edit This Template Using Creately.
Related Post: