Vulnerability Management Process Template
Vulnerability Management Process Template - Steps, benefits, and a free template. Assessment is the first stage of the cycle. An automated tool used to detect security weaknesses in a system or network. Web free vulnerability management policy template as both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Web vulnerability management resources. Web the first steps performed by the vmt are to: Web prioritization phase discovered vulnerabilities and assets are reviewed, prioritized, and assessed using results from technical and risk reports planning phase mitigation efforts. Web vulnerability management policy template. Web the dod vulnerability management process is the cyclical practice of five steps to identify, classify, remediate, and mitigate vulnerabilities. Free resource download our free vulnerability management policy template now. Web the dod vulnerability management process is the cyclical practice of five steps to identify, classify, remediate, and mitigate vulnerabilities. Steps, benefits, and a free template. Determine the scope of vulnerability management. Web establish rules for mitigating vulnerabilities with this vulnerability management policy. Assessment is the first stage of the cycle. Ad find vulnerability management in computers & tech books on amazon. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Web definitions vulnerability scan: Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web vulnerability management is a continuous, proactive,. Web vulnerability management is the process of prioritizing and minimizing those risks. Web the dod vulnerability management process is the cyclical practice of five steps to identify, classify, remediate, and mitigate vulnerabilities. Create a bug in storyboard or launchpad if one does not yet exist check that the report indicates the correct project. Web definitions vulnerability scan: Web quality data. Web implementing a vulnerability management process. Web quality data model (qdm) categories with recommended code systems. This paper looks at how a vulnerability management (vm) process could be designed and implemented within. Web establish rules for mitigating vulnerabilities with this vulnerability management policy. The quality data model (qdm) categories with the office of the. Web this vulnerability management policy: Web the first steps performed by the vmt are to: Perform vulnerability scan at the heart of a typical vulnerability management tool is a vulnerability scanner. An automated tool used to detect security weaknesses in a system or network. Web vulnerability management resources. Outlines the expectations, requirements, basic procedures for: Web vulnerability management resources. Free resource download our free vulnerability management policy template now. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web the vulnerability management guide should help to breakdown vulnerability management process into a manageable repeatable. Web free vulnerability management policy template as both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Web definitions vulnerability scan: Determine the scope of vulnerability management. Web the first steps performed by the vmt are to: Ad find vulnerability management in computers & tech books on amazon. Web implementing a vulnerability management process. Web vulnerability management resources. Create a bug in storyboard or launchpad if one does not yet exist check that the report indicates the correct project. An automated tool used to detect security weaknesses in a system or network. Web establish rules for mitigating vulnerabilities with this vulnerability management policy. Web the first steps performed by the vmt are to: Web establish rules for mitigating vulnerabilities with this vulnerability management policy. Web vulnerability management is the process of prioritizing and minimizing those risks. Web vulnerability management policy template. The scan consists of four stages: Steps, benefits, and a free template. Web free vulnerability management policy template as both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Web vulnerability management is the process of prioritizing and minimizing those risks. An automated tool used to detect security weaknesses in a system or network. Perform vulnerability scan at the heart. Free resource download our free vulnerability management policy template now. Web establish rules for mitigating vulnerabilities with this vulnerability management policy. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Web definitions vulnerability scan: Web the vulnerability management guide should help to breakdown vulnerability management process into a manageable repeatable cycles tailored to your. Steps, benefits, and a free template. Stay current with free resources focused on vulnerability management. Web vulnerability management policy template. Assessment is the first stage of the cycle. An automated tool used to detect security weaknesses in a system or network. Determine the scope of vulnerability management. Web vulnerability management is the process of prioritizing and minimizing those risks. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Ad find vulnerability management in computers & tech books on amazon. Web the dod vulnerability management process is the cyclical practice of five steps to identify, classify, remediate, and mitigate vulnerabilities. Web implementing a vulnerability management process. Web vulnerability management resources. This paper looks at how a vulnerability management (vm) process could be designed and implemented within. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web establish rules for mitigating vulnerabilities with this vulnerability management policy. An automated tool used to detect security weaknesses in a system or network. Determine the scope of vulnerability management. Web this vulnerability management policy: Stay current with free resources focused on vulnerability management. Web the first steps performed by the vmt are to: Outlines the expectations, requirements, basic procedures for: The scan consists of four stages: Ad find vulnerability management in computers & tech books on amazon. Web the dod vulnerability management process is the cyclical practice of five steps to identify, classify, remediate, and mitigate vulnerabilities. Web implementing a vulnerability management process. Steps, benefits, and a free template. Create a bug in storyboard or launchpad if one does not yet exist check that the report indicates the correct project. This paper looks at how a vulnerability management (vm) process could be designed and implemented within. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Free resource download our free vulnerability management policy template now.Wintel Interview Questions & Answers
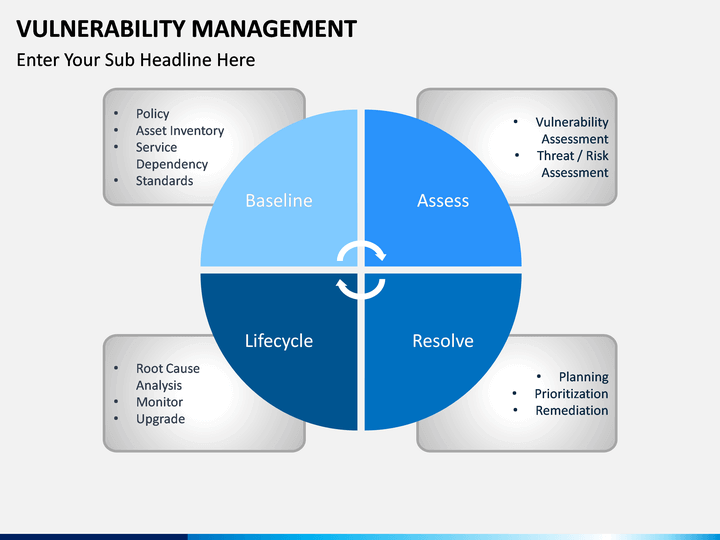
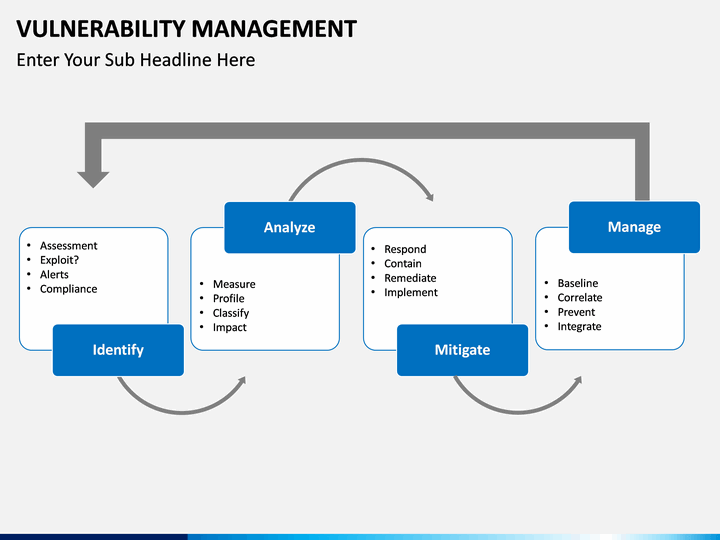
Vulnerability Management PowerPoint Template SketchBubble
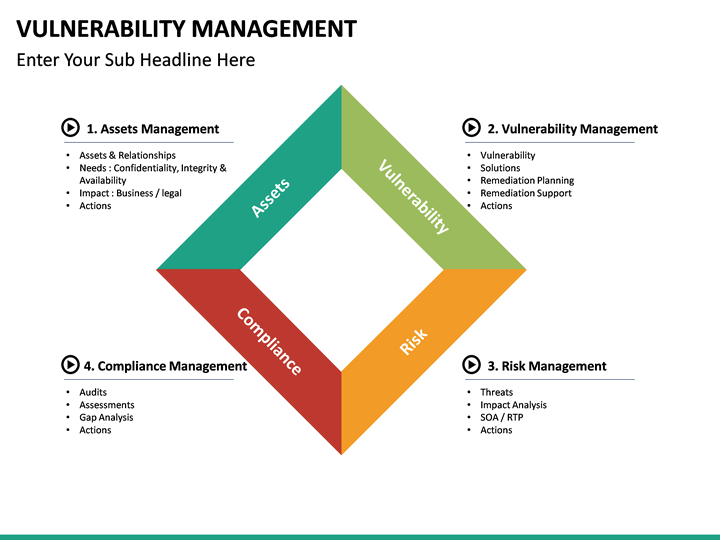
Vulnerability Management PowerPoint Template SketchBubble
Vulnerability Assessment and Testing Services Cloud4C
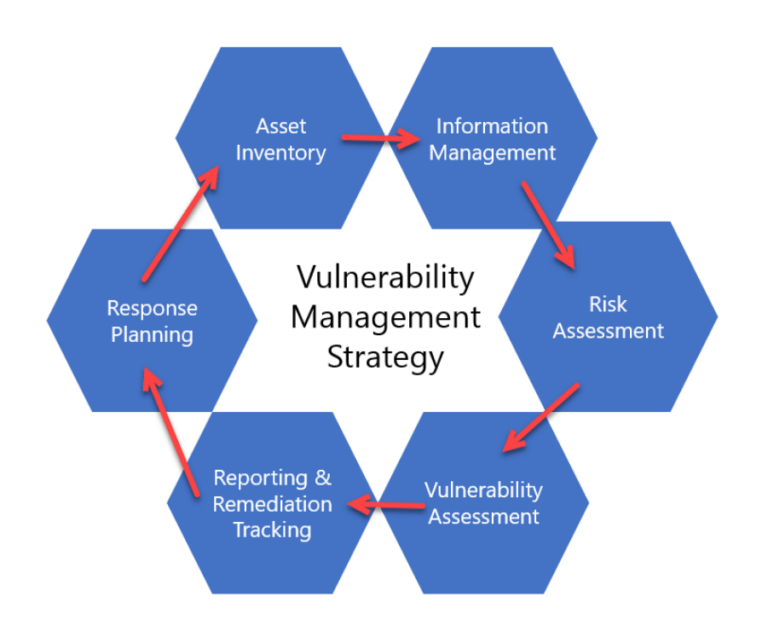
Creating a Vulnerability Management Strategy zSecurity
Figure 10 Vulnerability Assessment Flow Chart (Adapted from the US DOE
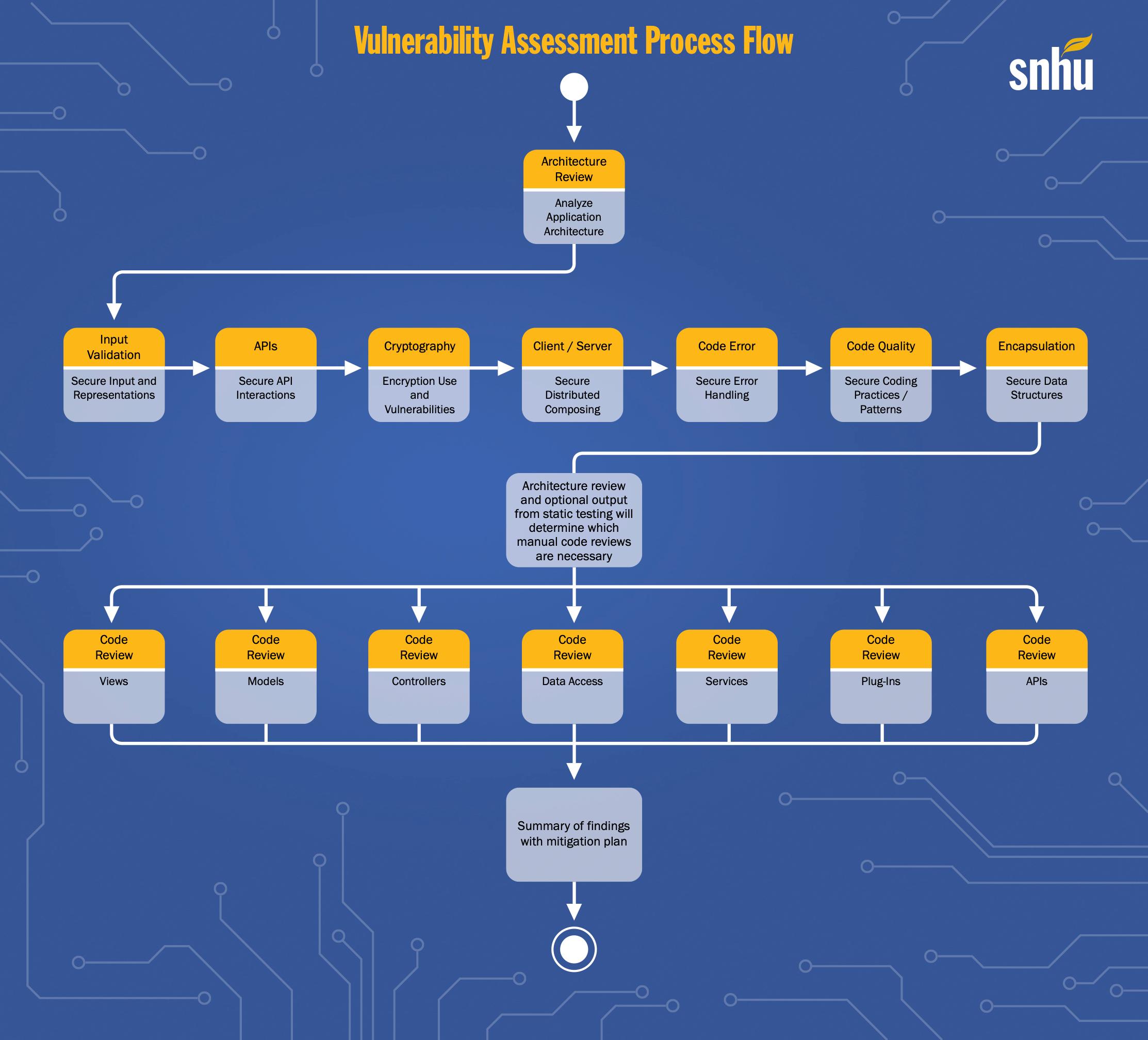
Vulnerability Assessment Process Flow snhu Architecture Review Analyze
Vulnerability Management PowerPoint Template SketchBubble
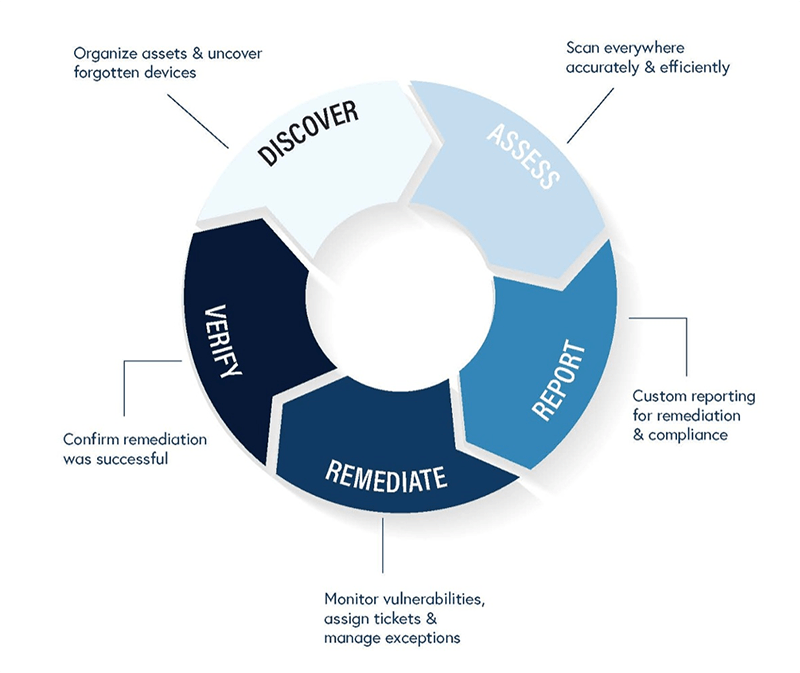
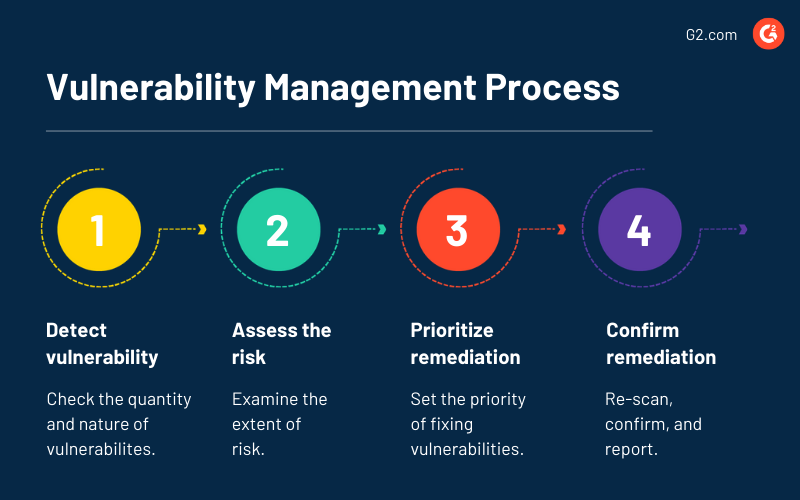
What Is Vulnerability Management? Get the Answers You Need
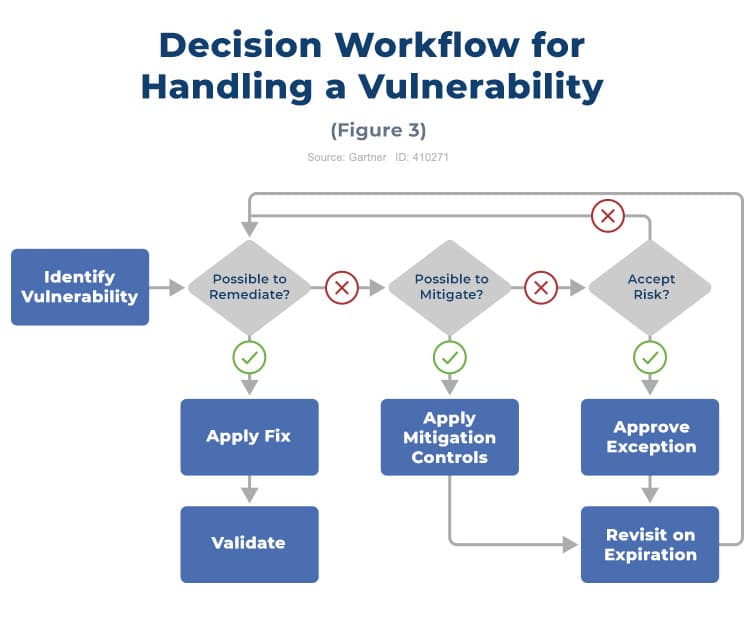
Vulnerability Management Process Flow Chart Rootshell
Web Vulnerability Management Policy Template For Cis Control 7 Cybersecurity Professionals Are Constantly Challenged By Attackers Actively Searching For Vulnerabilities Within.
Web Free Vulnerability Management Policy Template As Both An Example And A Starting Point, Esecurity Planet Has Developed A Free Vulnerability Management Policy.
Web Quality Data Model (Qdm) Categories With Recommended Code Systems.
Web Vulnerability Management Resources.
Related Post: