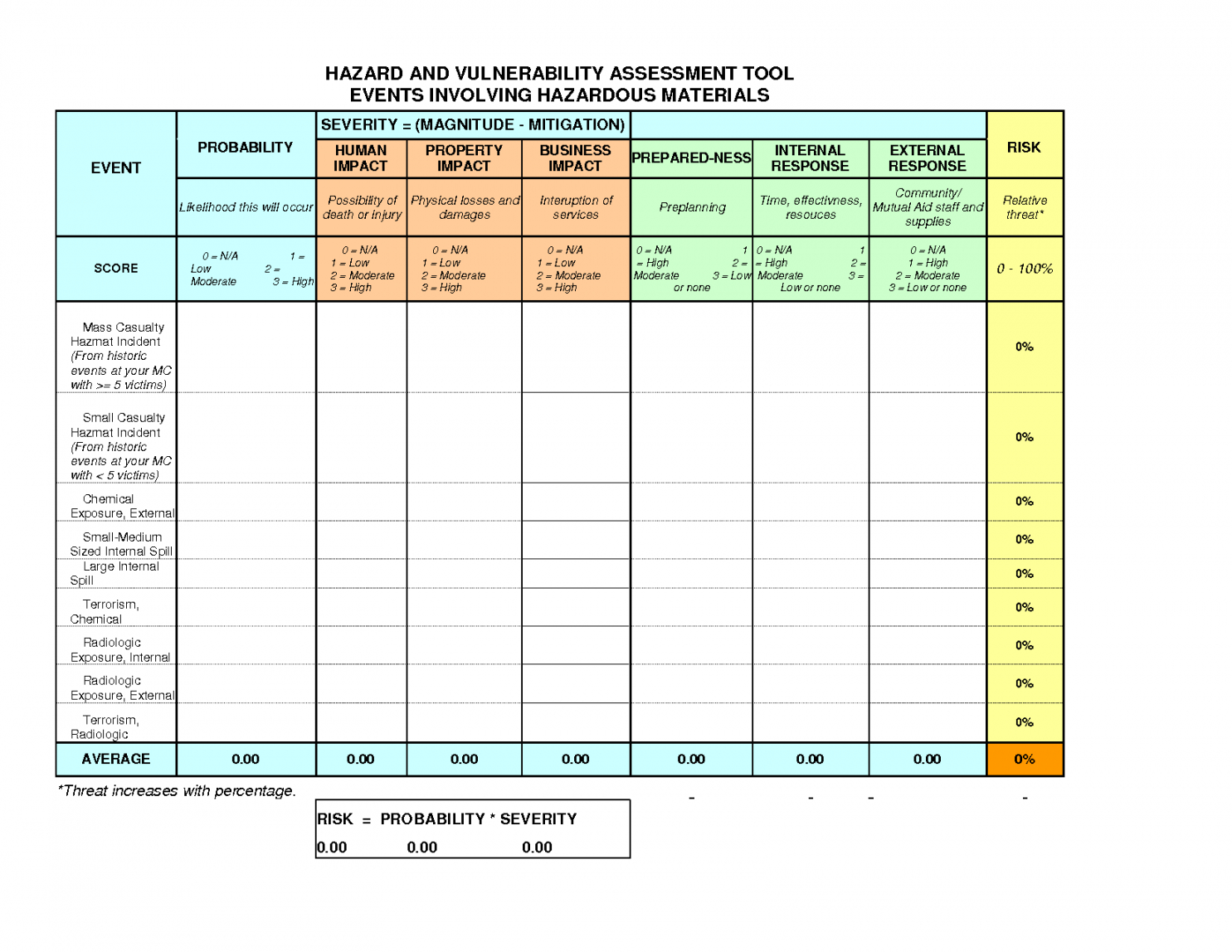
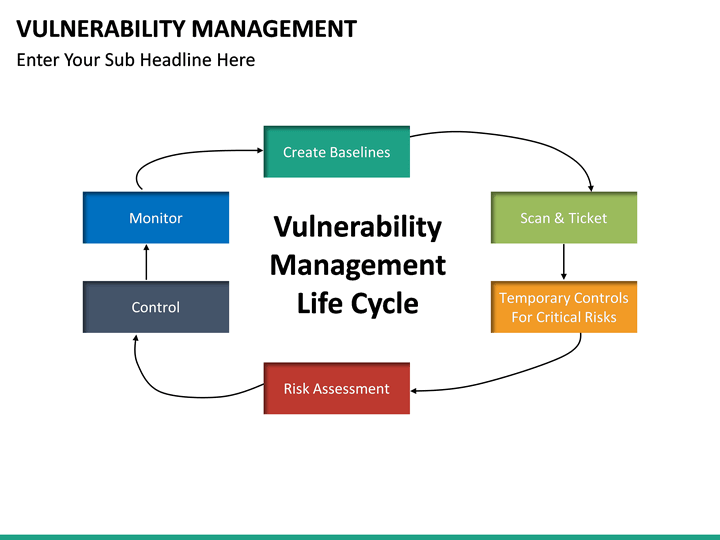
Vulnerability Management Template
Vulnerability Management Template - Web 6 hours agomore than 86 percent of union members approved the contract, the international brotherhood of teamsters said tuesday. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Ups employees covered by the. Vulnerabilities occur through product defects, misconfigurations, or. At gitlab we identify vulnerabilities in a number of different. Web vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Web vulnerability management is the continual process of identifying, prioritizing, mitigating and remediating vulnerabilities. Web it vulnerability management standard i. Creating and implementing an vulnerability management policies and procedures is a vital component of any company’s cyber. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to. Web vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them.. Web vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them. Web i am excited to be applying for the position of vulnerability management. In the previous role, i. Web vulnerability management is the continual process of identifying, prioritizing, mitigating and remediating vulnerabilities. Determine the scope of. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to. Defend against threats and respond quickly to hidden cyber attacks across endpoints. Web vulnerability management policy template. Ups employees covered by the. Vulnerabilities occur through product defects, misconfigurations, or. Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. Yet, as indicated by the wave of massive data breaches and ransomware attacks,. Web vulnerability management is a continuous, proactive, and often automated process that. Web vulnerability management policy template. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Determine the scope of vulnerability management. Yet, as indicated by the wave of massive data breaches and ransomware attacks,. Ups employees covered by the. Web it vulnerability management standard i. At gitlab we identify vulnerabilities in a number of different. Ups employees covered by the. Please accept this letter and the attached resume as my interest in this position. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web vulnerability management is the continual process of identifying, prioritizing, mitigating and remediating vulnerabilities. Vulnerabilities occur through product defects, misconfigurations, or. Determine the scope of vulnerability management. Web download our free vulnerability management policy template now. Web download your template today! Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. Overview security vulnerabilities enable attackers to compromise a resource or data. Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Web who is the vulnerability management plan template for? Web it vulnerability management standard. Creating and implementing an vulnerability management policies and procedures is a vital component of any company’s cyber. Web who is the vulnerability management plan template for? Web vulnerability management is the continual process of identifying, prioritizing, mitigating and remediating vulnerabilities. Web network vulnerability types could be categorized but not limited: A vulnerability is a weakness in an application (frequently a. Yet, as indicated by the wave of massive data breaches and ransomware attacks,. Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Determine the scope of vulnerability management. Web i am excited. Web every vulnerability should follow this template. In the previous role, i. This vulnerability management plan template is designed for it leaders and teams who are looking to create a plan to. Overview security vulnerabilities enable attackers to compromise a resource or data. Download template purpose the purpose of the (company) vulnerability management policy. Web who is the vulnerability management plan template for? Determine the scope of vulnerability management. Web free vulnerability management policy template as both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Defend against threats and respond quickly to hidden cyber attacks across endpoints. Please accept this letter and the attached resume as my interest in this position. Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Web vulnerability management policy template. Ups employees covered by the. Web 6 hours agomore than 86 percent of union members approved the contract, the international brotherhood of teamsters said tuesday. Vulnerabilities occur through product defects, misconfigurations, or. Yet, as indicated by the wave of massive data breaches and ransomware attacks,. Purpose this standard supports and supplements fsu technology policies and provides additional security and privacy best. Web in this paper, we provide an overview of how we go about managing vulnerabilities in our products and infrastructure, and how we’re constantly evolving that approach by. Web vulnerability management is the continual process of identifying, prioritizing, mitigating and remediating vulnerabilities. Web i am excited to be applying for the position of vulnerability management. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to. Web download our free vulnerability management policy template now. Ups employees covered by the. In the previous role, i. Web every vulnerability should follow this template. Yet, as indicated by the wave of massive data breaches and ransomware attacks,. Overview security vulnerabilities enable attackers to compromise a resource or data. Web i am excited to be applying for the position of vulnerability management. Vulnerabilities occur through product defects, misconfigurations, or. This vulnerability management plan template is designed for it leaders and teams who are looking to create a plan to. Defend against threats and respond quickly to hidden cyber attacks across endpoints. Web vulnerability management policy template. Web network vulnerability types could be categorized but not limited: Web who is the vulnerability management plan template for? Please accept this letter and the attached resume as my interest in this position. Web vulnerability management is the continual process of identifying, prioritizing, mitigating and remediating vulnerabilities.Editable Updated Guidelines For Fast Systems In Hazard Assessment
Vulnerability Management IT Security Standard Templates at
Vulnerability Management PowerPoint Template SketchBubble
Free Vulnerability Assessment Templates Smartsheet
Hazard Vulnerability Assessment Template Templates OTIzMTc Resume
Sample Hazard Vulnerability Analysis Analysis, Vulnerability
Creating a Vulnerability Management Strategy Dr. Erdal Ozkaya
Vulnerability Management Policy Template in 2021 Patch management
Vulnerability Assessment Flow Chart (Adapted from the US DOE 2002
Fresh Vulnerability Management Program Template Sparklingstemware
Web Download Your Template Today!
Getapp.com Has Been Visited By 100K+ Users In The Past Month
Web Develop A Plan To Continuously Assess And Track Vulnerabilities On All Enterprise Assets Within The Enterprise’s Infrastructure, In Order To Remediate, And.
At Gitlab We Identify Vulnerabilities In A Number Of Different.
Related Post: